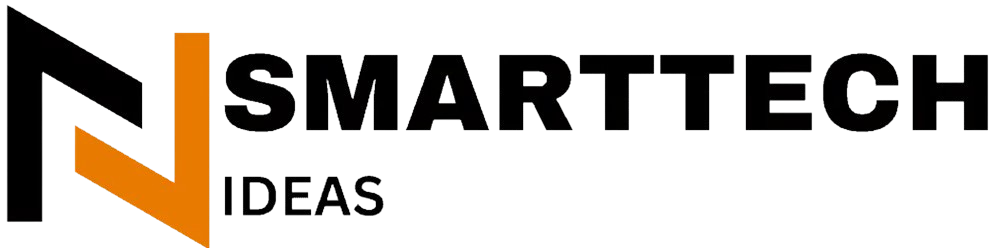Best Database Activity Monitoring Solutions Made Simple: From Setup to Success

Database activity monitoring solutions don’t log enough activity data by default. This creates major security gaps for organizations. Database activity monitoring solutions have become vital to protect sensitive information at a time when data breaches drive up costs, damage customer trust and trigger regulatory penalties.
Picking the right database activity monitoring vendor can feel daunting. Many organizations look to the database activity monitoring Gartner magic quadrant to guide their choice. Today’s DAM tools pack advanced features that include automated discovery, classification, and protection against SQL injections, insider threats, and malware attacks.
This piece breaks down what you need to know to set up a DAM system that works. We’ll share practical tips to help you build optimal security coverage for your Database Activity Monitoring Solutions. Our advice works whether you’re just starting with DAM or want to enhance your current setup.
What is Database activity monitoring solutions
“Without a systematic way to start and keep data clean, bad data will happen.”
— Donato Diorio, Founder and CEO of RingLead
Database activity monitoring solutions (DAM) works independently from database management systems. It watches and analyzes database activities as they happen. DAM solutions track all user actions, queries, and transactions without using native Database Activity Monitoring Solutions logs or audits, which sets them apart from regular database security measures.
Core components of DAM
DAM’s foundation consists of several essential components that create a detailed security framework. DAM tools track and record all database activity at the field level and store this information externally to keep it secure [1]. The solutions use network sniffing, memory scraping, and system table analysis.
A strong DAM system has:
- Independent monitoring features that track all SQL transactions (DML, DDL, DCL) with minimal impact on performance 0-2%
- External storage of audit logs separate from the Database Activity Monitoring Solutions
- Immediate analysis and combination of activities across multiple database management systems
Key benefits for businesses
DAM creates value in several ways. It makes an organization’s security stronger by spotting and stopping unauthorized access attempts. DAM solutions also help companies stay compliant with standards like PCI DSS, HIPAA, and SOX.
Businesses get these benefits from DAM:
- Enhanced Security Controls: DAM helps organizations spot potential threats through immediate monitoring and stops data breaches before they happen [1]. It also detects unusual activities from both inside and outside sources, which lets system administrators improve their data protection measures.
- Comprehensive Audit Capabilities: DAM solutions keep detailed audit trails that are a great way to get forensic analysis during investigations. These audit features help during compliance checks by showing clear patterns of Database Activity Monitoring Solutions access and possible security issues.
- Operational Efficiency: DAM tools spot performance bottlenecks and help optimize resource use through advanced monitoring methods. This results in better database performance and less system downtime.
- Customer Trust Enhancement: Companies can better assure their customers about data protection by keeping clear audit trails of all Database Activity Monitoring Solutions. The system also prevents unauthorized changes to critical data, which keeps data integrity intact.
How to Choose the Right DAM Solution

Picking the right Database activity monitoring solutions needs a good review of what your organization needs and what’s available. You’ll get a DAM system that matches your security goals when you take a systematic approach.
Assess your database environment
Your first step should be getting a full picture of your current Database Activity Monitoring Solutions infrastructure. Think about which databases you need to monitor – most DAM products support Oracle, Microsoft SQL Server, IBM DB2, MySQL, and Sybase. In spite of that, vendors update their compatibility lists often, so you should ask each provider for their latest database support documentation.
Compare DAM vendors
When reviewing DAM vendors, these aspects matter most:
- Integration Capabilities: Look for solutions that provide continuous connection with your existing tools and software
- Performance Impact: Pick tools that don’t slow down database operations, typically 0-2% performance overhead
- Scalability Features: Your solution should grow as your organization expands
- Security Features: Review the encryption capabilities and how well they follow relevant regulations
Evaluate costs and ROI
DAM solutions’ pricing models differ substantially between vendors. Some vendors base their costs on processor cores, while others use different metrics. Here’s how to calculate ROI:
- Measure the time you save with automated monitoring
- Calculate your reduced risk exposure through boosted security controls
- Look at long-term maintenance and support costs
Check Gartner recommendations
Gartner research suggests choosing DAM solutions with:
- Advanced features to find and classify data
- Tools to manage vulnerabilities
- Capabilities to analyze at application level
- Ways to integrate identity and access management
- Complete risk management support
Your main focus should be solutions that monitor privileged users to meet compliance-related audit requirements. Tools that help manage threats to watch Database Activity Monitoring Solutions access are also worth considering. A careful review of these factors will help you pick a DAM solution that fits your organization’s security needs and gives you good value for money.
Setting Up Your DAM System
Setting up a Database activity monitoring solutions requires careful planning. Organizations can get the most out of their DAM systems and reduce disruptions with the right setup and integration.
Original configuration steps
The first significant step is to review your database environment with a detailed audit. This audit helps you identify the types of Database Management Systems (DBMs) and operating system versions that work with DAM agents.
A strong foundation needs:
- Static IP addresses for all predicted appliances
- Downloaded images and license keys
- Confirmation that your DAM software has current patches
- DNS, NTP, SNMP, SMTP, and syslog/SIEM servers setup
The next step after setup is to create security policies that outline acceptable database activities and access controls. You’ll need governance protocols with a matrix that connects users, roles, authorized operations, and types of assets. We focused on technical controls like encryption and multi-factor authentication to protect sensitive data.
Integration with existing Database activity monitoring solutions
Your network infrastructure needs good preparation for smooth integration. Database hosts should be properly separated from administrator workstations and firewalls. The next step is to check current firewall policies for correct port access between your DAM system, database servers, and administrative workstations.
The best integration needs:
- Clear objectives to make content workflows efficient and improve collaboration
- A review of DAM’s compatibility with existing systems like content management systems and marketing automation platforms
- A reliable data migration strategy for a smooth transition
- Consistent metadata tagging across your tech stack
The DAM solution should use only 1-3% of disk resources and CPU with an agent-only collection method. Regular system performance checks help address integration problems quickly to protect your Database Activity Monitoring Solutions environment continuously .
Common DAM Implementation Challenges
“The human side of analytics is the biggest challenge to implementing big data.”
— Paul Gibbons, Author and Management Consultant
Organizations run into many roadblocks in their Database activity monitoring solutions trip, even with careful planning. Teams can develop strategies that work when they know these challenges well.
Performance impact issues
Database administrators worry most about system performance when they set up DAM solutions. Profilers, logging mechanisms, and monitoring tools can slow down database operations. Simple monitoring tools like Activity Monitor use technologies that affect server performance.
To keep performance at its best:
- DAM system should use only 1-3% of disk and CPU resources
- Watch network bandwidth closely since poor connections hurt throughput
- Fix storage system bottlenecks quickly to avoid high disk latency problems
Security configuration problems
Outdated equipment and weak protection measures create most security configuration problems. Small facilities don’t have important security safeguards, especially in their operational technology networks. So operators don’t deal very well with:
- Hard-coded and default passwords that never change
- Poor visibility into operational network traffic
- Not enough expertise to watch for new threats
- Poor documentation of vulnerability checks
User adoption barriers
DAM implementation success depends on how well users accept and use the system. Companies often face resistance because of complex technical issues and workflow changes. The biggest adoption hurdles are:
- Technical Complexity: Users get frustrated and resist when they face steep learning curves
- Workflow Disruptions: Teams don’t like new systems when they see extra work coming their way
- Training Gaps: Poor training resources and support documents make it hard to use the system well
Companies should set up efficient platforms that match their users’ basic needs to overcome these barriers. The core team should also pick DAM champions in each group to help their peers and reduce IT support workload. Regular user feedback through surveys and digital forums helps improve the system continuously.
Conclusion
Database activity monitoring solutions is a vital defense against modern data security threats. This piece explores how DAM solutions protect sensitive information and ensure compliance while optimizing operations with minimal performance effects.
DAM’s success depends on smart vendor selection and implementation planning. Organizations achieve the best results when they balance security needs with user experience. The resource usage stays between 1-3% while maintaining complete monitoring capabilities.
Note that DAM implementation begins a continuous trip rather than reaching a destination. System updates, user training and security assessments help organizations be proactive against emerging threats. The knowledge from this piece enables you to implement DAM with confidence, and you’ll know the right steps to take and pitfalls to avoid.
FAQs
Q1. What are the key components of Database Activity Monitoring (DAM)?
DAM systems typically include independent monitoring capabilities, secure external storage for audit logs, and real-time correlation of activities across multiple database management systems. These components work together to provide comprehensive security and monitoring of database activities.
Q2. How does Database activity monitoring solutions impact database performance?
When implemented correctly, DAM solutions have minimal impact on database performance. Most efficient DAM tools consume only 1-3% of disk and CPU resources, ensuring that database operations remain smooth while providing robust security monitoring.
Q3. What are the main benefits of implementing a DAM solution?
DAM solutions offer enhanced security controls, comprehensive audit capabilities, improved operational efficiency, and increased customer trust. They help prevent data breaches, facilitate compliance with regulations, and provide valuable insights for optimizing database performance.
Q4. How should organizations choose the right DAM solution?
When selecting a DAM solution, organizations should assess their database environment, compare vendors based on integration capabilities and security features, evaluate costs and ROI, and consider recommendations from industry analysts like Gartner. It’s crucial to choose a solution that aligns with specific security objectives and scalability needs.
Q5. What are common challenges in implementing DAM, and how can they be addressed?
Common challenges include performance impact issues, security configuration problems, and user adoption barriers. To address these, organizations should carefully monitor system resources, ensure proper security configurations, and focus on user training and support. Implementing streamlined platforms and appointing DAM champions within teams can also help overcome adoption hurdles.
Read More: NVIDIA RTX 5080 vs. RTX 4090